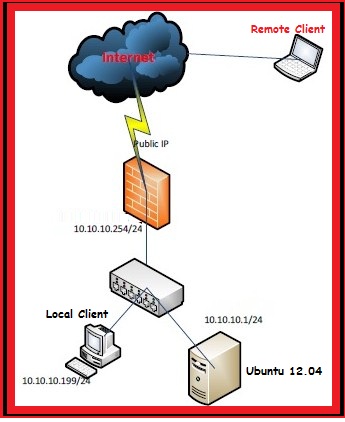
This tutorial describes that how to configure the OpenVPN Server in Ubuntu and clients in Windows XP/7.
I am taking the scenario of SOHO network, which is protected by Firewall, we’ll implement the OpenVPN on internal Ubuntu server to access the internal SOHO network (Server and PCs) through the internet from anywhere securely.
OpenVPN Server Installation:
Install the openvpn package using the following command:
sudo apt-get install openvpn

On Ubuntu 14.04 LTS, please use the following command to install the openvpn package:
sudo apt-get install openvpn easy-rsa
Make an easy-rsa directory inside /etc/openvpn:
cd /etc/openvpn/
sudo mkdir easy-rsa
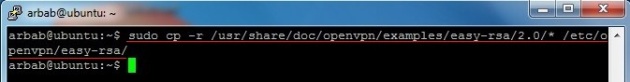
 Copy the default easy-rsa into /etc/openvpn for setting up Certificate Authority (CA), certificates and keys generation for OpenVPN server and clients:
Copy the default easy-rsa into /etc/openvpn for setting up Certificate Authority (CA), certificates and keys generation for OpenVPN server and clients:
sudo cp -r /usr/share/doc/openvpn/examples/easy-rsa/2.0/* /etc/openvpn/easy-rsa/
 On Ubuntu 14.04 LTS, use the following command to copy the default easy-rsa into /etc/openvpn for setting up Certificate Authority (CA), certificates and keys generation for OpenVPN server and clients:
On Ubuntu 14.04 LTS, use the following command to copy the default easy-rsa into /etc/openvpn for setting up Certificate Authority (CA), certificates and keys generation for OpenVPN server and clients:
cp -r /usr/share/easy-rsa/* /etc/openvpn/easy-rsa/
Edit /etc/openvpn/easy-rsa/vars:
cd /etc/openvpn/easy-rsa/
sudo nano vars
 Edit these parameters according to your need:
Edit these parameters according to your need:
export KEY_COUNTRY="US"
export KEY_PROVINCE="NC"
export KEY_CITY="Winston-Salem"
export KEY_ORG="Example Company"
export KEY_EMAIL="me@example.com"
 Login as root user to perform next few steps:
Login as root user to perform next few steps:
su -
 Move to the /etc/openvpn/easy-rsa/ and enter these commands:
Move to the /etc/openvpn/easy-rsa/ and enter these commands:
cd /etc/openvpn/easy-rsa/
source vars
./clean-all

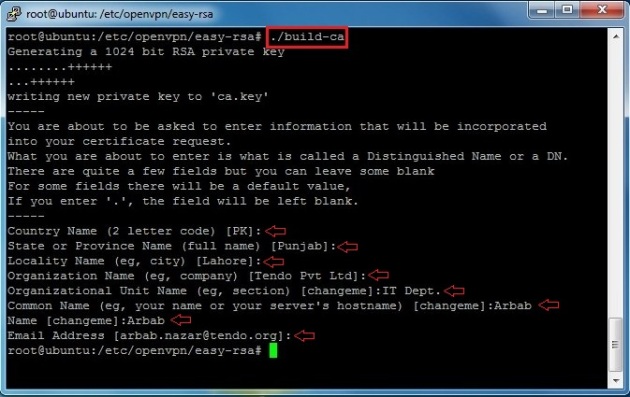
Now, generate the CA certificate and key:
./build-ca

To resolve this error, we need to copy the openssl-1.0.0.cnf file into openssl.cnf:
cp openssl-1.0.0.cnf openssl.cnf

Again, try to generate the CA certificate and key:
./build-ca
Next, generate a server certificate and private key:
./build-key-server tendo
 Note: tendo is my server name in above command, you can use your server name here.
Note: tendo is my server name in above command, you can use your server name here.
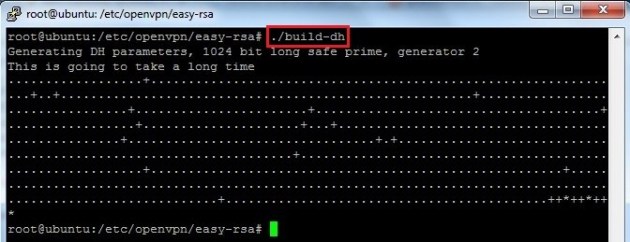
For OpenVPN server,Diffie Hellman parameters are must:
./build-dh
Copy all the certificates and keys into /etc/openvpn/ from key/ subdirecotory:
cd keys/
cp ca.crt tendo.crt tendo.key dh1024.pem /etc/openvpn/

Logout from root user:
exit
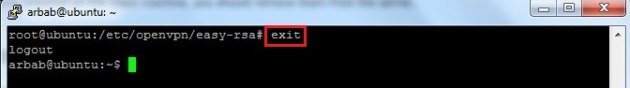
Copy the sample config file into /etc/openvpn/:
sudo cp /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz /etc/openvpn/
Unpack the server.conf.gz:
sudo gzip -d /etc/openvpn/server.conf.gz

Edit the /etc/openvpn/server.conf file and enter the certificates and keys information that we have created above:
sudo nano /etc/openvpn/server.conf
Here is my server.conf file as an example, you can change it according to your requirement:
port 1194
proto udp
dev tun
ca ca.crt
cert tendo.crt
key tendo.key # This file should be kept secret
dh dh1024.pem
#VPN subnet for OpenVPN to draw client addresses from.
server 172.16.10.0 255.255.255.0
ifconfig-pool-persist ipp.txt
#Push routes to the client to allow it to reach other
#private subnets behind the server.
push "route 10.10.10.0 255.255.255.0"
#If you want that all of your Internet traffic pass
#through the VPN server then enable this
;push "redirect-gateway def1 bypass-dhcp"
# For name resolution, enable this
;push "dhcp-option DNS 10.10.10.254"
client-to-client
keepalive 10 120
comp-lzo
max-clients 10
persist-key
persist-tun
status openvpn-status.log
verb 3
mute 20

Now, start the OpenVPN server:
sudo /etc/init.d/openvpn start

Note: Forward udp port 1194 to your internal OpenVPN server on edge firewall
Client Certificates:
VPN client also need a certificate to authenticate itself to the server. Using the root user, create the different certificate for each client:
cd /etc/openvpn/easy-rsa/
source vars
./build-key arbabpc
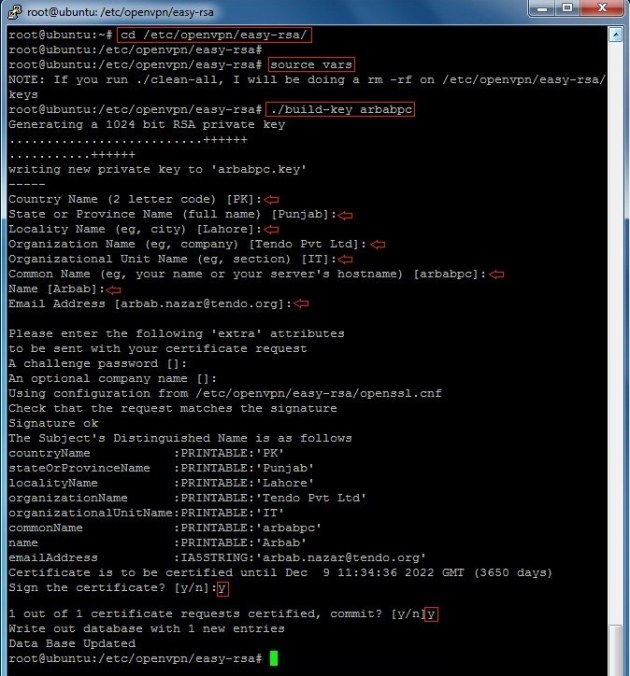 Note: arbabpc is my vpn client name in above command, you can use your client name here.
Note: arbabpc is my vpn client name in above command, you can use your client name here.
Copy these files to the client machine using winscp or any other method:
1) /etc/openvpn/ca.crt
2) /etc/openvpn/easy-rsa/keys/arbabpc.crt
3) /etc/openvpn/easy-rsa/keys/arbabpc.key
Your files name will be differ, so adjust them as per your need.
OpenVPN Client Configuration on Windows Machine:
Download free OpenVPN client for windows from here, and install it. Below is the step by step procedure to configure this OpenVPN client in order to connect to the OpenVPN server that we have configured above:









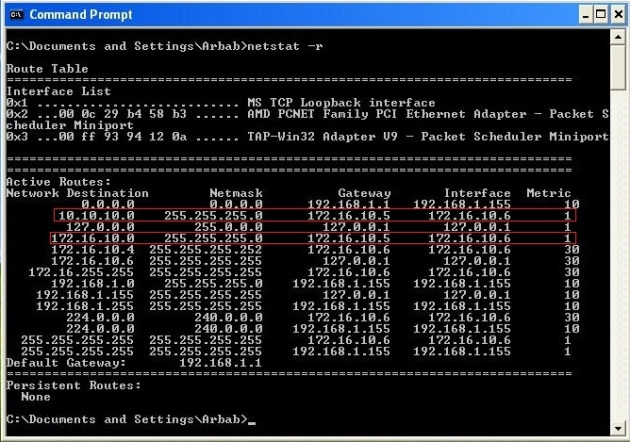
Check the routing table on client machine:
netstat -r
Ping to the OpenVPN internal ip:

For internal host, the ping will be failed because internal host doesn’t know about this vpn pool. To overcome this problem, we need to configure nat on OpenVPN server:
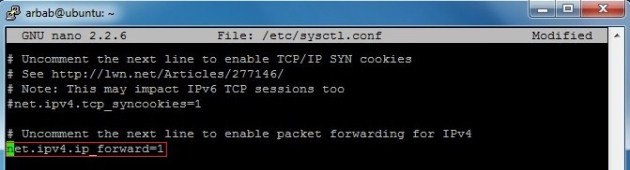
Edit the /etc/sysctl.conf file:
sudo nano /etc/sysctl.conf

Uncomment the following line:
net.ipv4.ip_forward=1
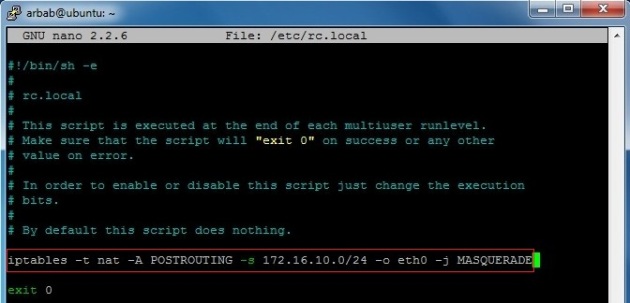
Edit the /etc/rc.local file:
sudo nano /etc/rc.local

Add the iptables rule there:
iptables -t nat -A POSTROUTING -s 172.16.10.0/24 -o eth0 -j MASQUERADE
Reboot your OpenVPN server or issue these commands as root user:
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -t nat -A POSTROUTING -s 172.16.10.0/24 -o eth0 -j MASQUERADE
Ping to the internal host again:
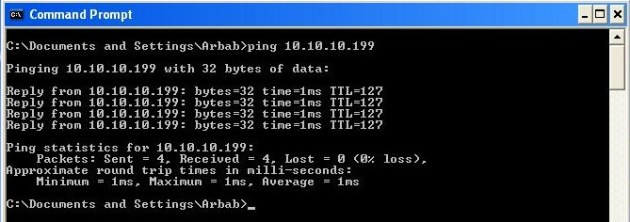
Success 🙂
Hope this will help you!
Please Remember me in your prayers!
Enjoy 








































Hello Arbab,
This is a great guide, thanks for making it! I have one question though. I don’t get how these certificates are any secure, if somebody copies those files from the VPN client, he can easily connect with the server, or can’t he? As I see it, username/password authentication is much more secure than these certificates.. or am I wrong in thinking this?
I’m looking forward to your response, please bear in mind that I don’t have any real experience concerning Linux and network security.
John
Hi John
In this example the security rests upon control of the certificates, so if they fall into the wrong hands anyone can use them. If the certificates are compromised then they can be revoked so that they can no longer to be used.
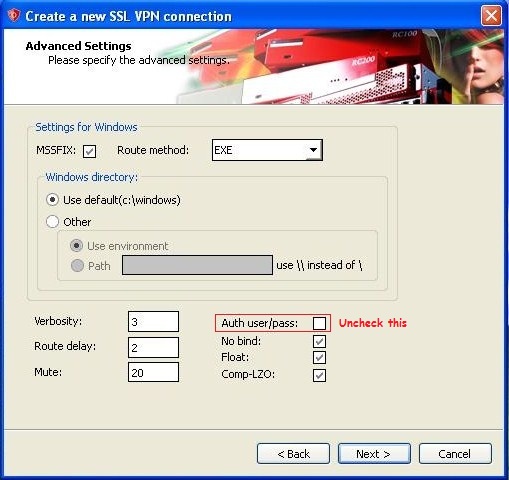
There is an option to generate a client certificate with a password (challenge password). We’ve created a certificate with a password too for an extra layer of security. Plus you’ll notice in the above example that auth user/pass is unticked – if you select this option you can force the user to authenticate on login too.
Mike
Arbab,
Do you have any ideas for a good way to monitor the VPN server? Ideally I’d like to create an on connect script to let us know when someone connects (struggling to get sendmail working with our Exchange server though). A web interface/GUI would be good too, I know there’s things out there, I just don’t fully understand what we’ve got setup, it’s working well at the moment, and I don’t want to break it!
Many thanks, Michael
this is a good tutorial for like me being a newbies in linux world.. thank you